Security Copilot Promptbook: Threat Actor Profile
Discover how Security Copilot transforms threat actor data into actionable intelligence for effective cyber defense strategies.

Most attacks, whether complex or simple, motivated by different reasons, typically share one common element: a person controlling the keyboard. While automation can assist in the initial stages of a compromise, the execution of objectives generally involves another individual at a workstation, much like yourself. Humans, being habitual, often struggle to completely conceal their digital traces, no matter how cautious they are. These digital breadcrumbs are what security researchers track to attribute attacks and gain insight into their adversaries. By comprehending the tactics, techniques, and procedures (TTPs) used, defenders can gain an advantage in staying ahead.
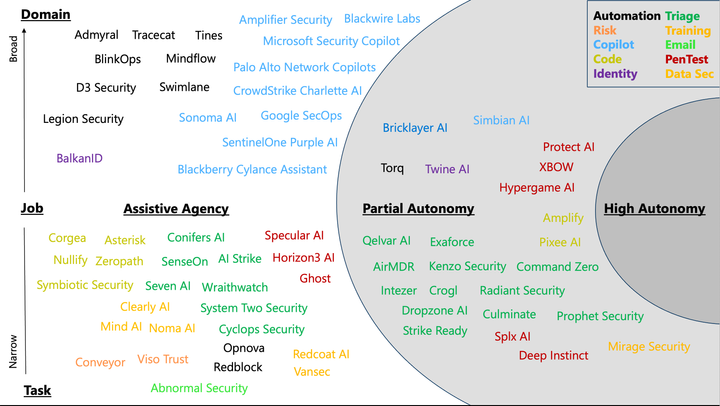
Threat naming is a core part of the security industry and broader adversary understanding. Public and private sectors organizations use the insights and information at their disposal to help form profiles of who is or might target their business. What used to be reserved mostly within the government is now very mainstream and part of day-to-day security operations. This explosion of information about threat actors, their tools and the vulnerabilities they exploit can be difficult to keep up with and organize. Between different actor names to complex campaign tracking, organizations can struggle to understand which threat actors matter to them and how to best operationalize the data.
In this post, I will demonstrate leveraging generative AI to go from threat actor name, all the way to a fleshed out profile within a matter of minutes using Security Copilot and the Threat Actor Profile promptbook. The example actor we will use is Storm-0216, a reference back to the previous promptbook on automating a vulnerability impact assessment posting. All the threat intelligence information is being sourced from Microsoft Defender Threat Intelligence which is included with Security Copilot.
Promptbook Demonstration
For those who prefer to see more of a live demonstration, I put together a brief video explaining the basic controls within Security Copilot and myself walking through the Promptbook that's been created.
Prompt Walkthrough
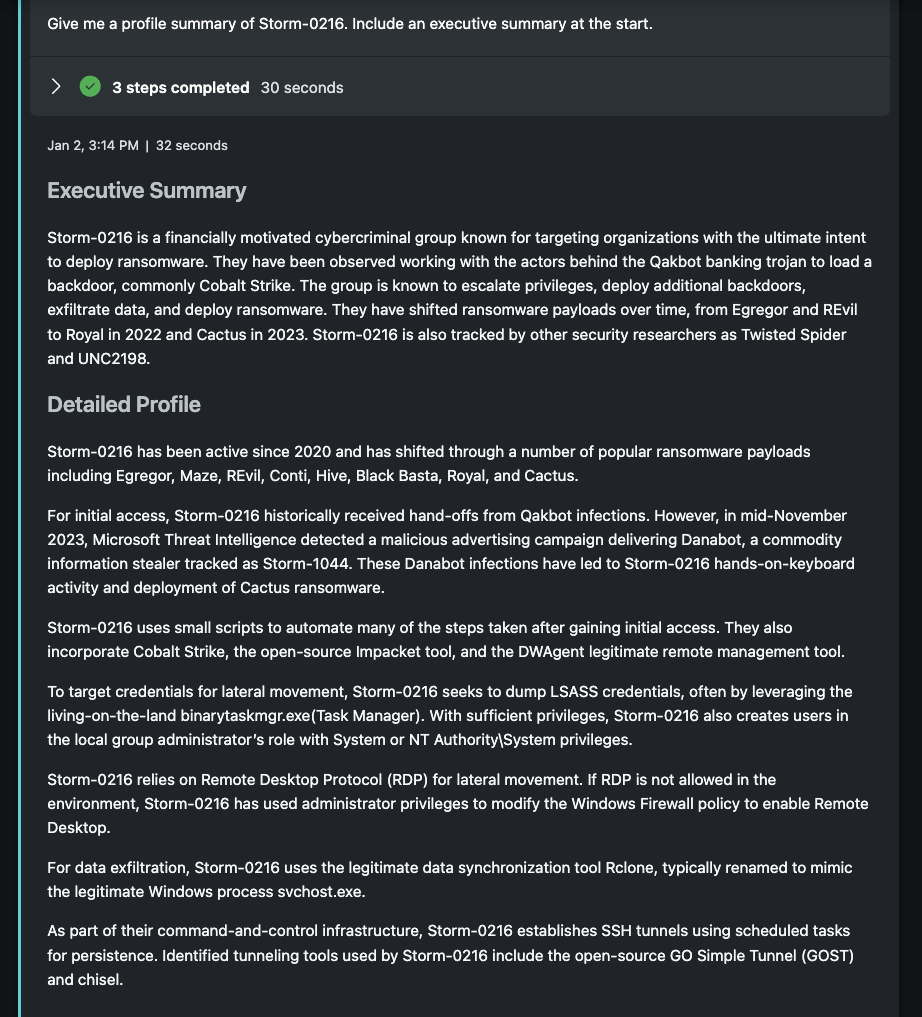
The first step within this Promptbook is to ask for a profile of the named threat I want to know more about. Storm-0216 was an attractive target as the group was making use of a recent vulnerability I had used in my previous promptbook example. The prompt is simple and open, generating an executive summary and filling in whatever else Security Copilot knows about the threat. Normally, I like to refine prompts to deliver specific results, but an open prompt like this allows us to seed the session with useful context that can be helpful later.
Within the initial summary, I see accurate information and a preview of the jargon across the industry. This group goes by other names like Twisted Spider and UNC2198. They also make use of several different tools and backdoors, each with their own unique names and explanations. Knowing nothing about this group, this response is a helpful start to get acquainted, though it's a bit overwhelming. In the next prompts, I will narrow in on key areas and transform this data into something an organization could better operationalize.
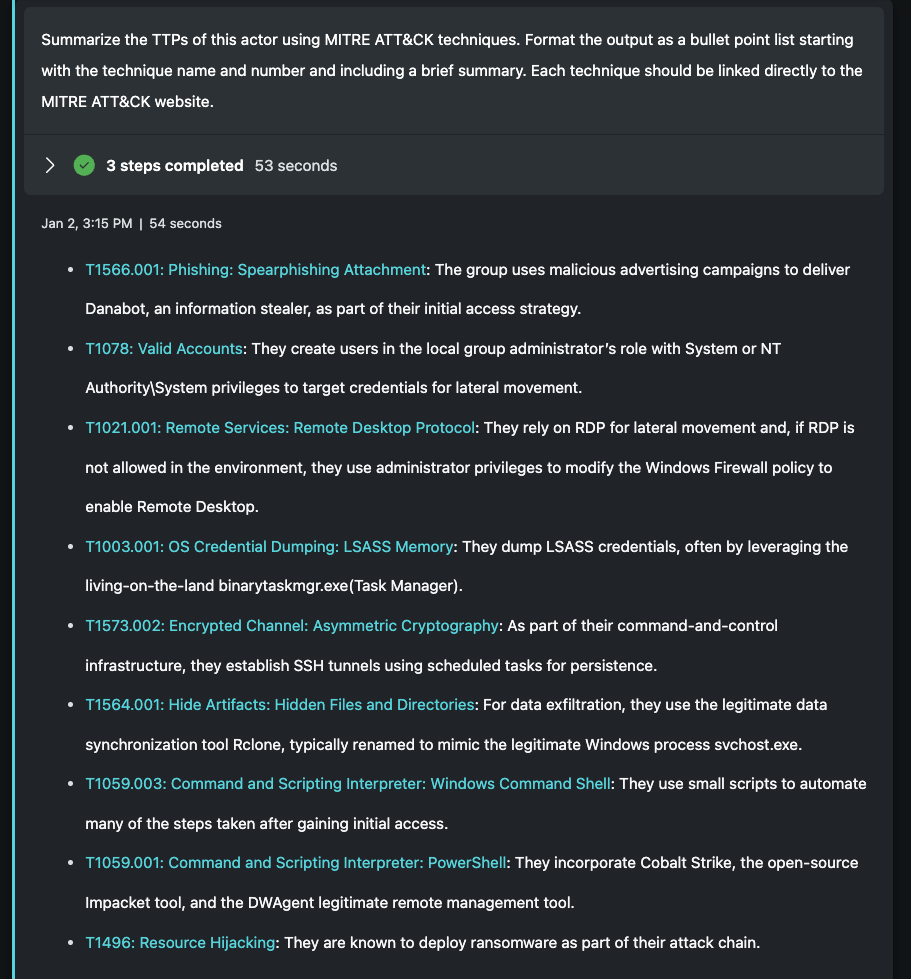
Here, our prompt is more specific, both in the request and the format. I've asked Security Copilot to align what it knows about Storm-0216 within the MITRE ATT&CK framework. Without specifying this, I get useful results, but they are less organized and difficult to parse. I really like this alignment as the ATT&CK framework is leveraging across multiple solutions and companies, giving defenders a common taxonomy to reference. By requesting that data be mapped to this framework, it becomes more actionable.
For the format, I specify a bullet list and explicitly request the name and number of the MITRE technique along with a brief summary. Without this level of detail, I find that the responses will vary across each Promptbook run which isn't ideal, though very much a normal outcome when using generative AI. Finally, there's a request to link each technique to its given MITRE page for deeper explanation. I find this helpful as a quick reference to learn more. This view could alternatively be expressed as a table, though the bullet list is easier to consume.
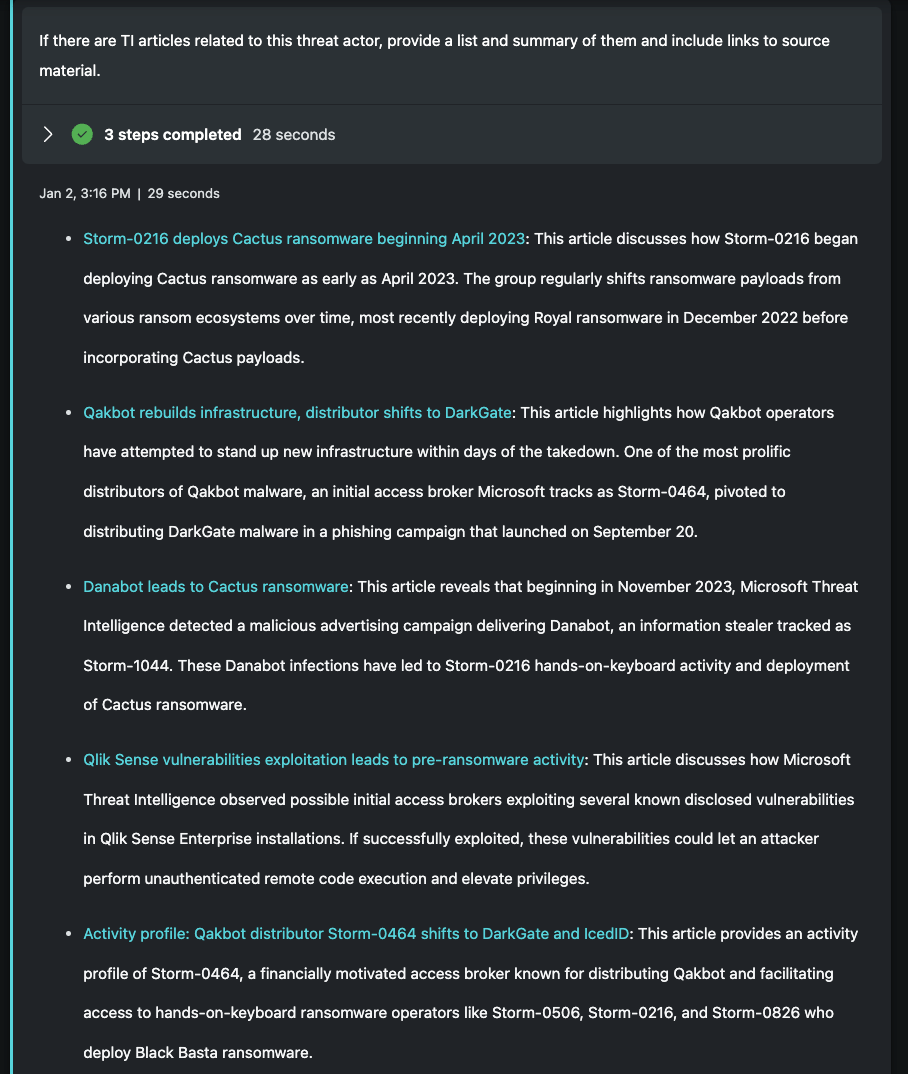
This prompt performs a basic look-up within the database of curated and OSINT aggregated intelligence from Microsoft Defender Threat Intelligence. The prompt is simple and to the point. Provide any articles that include the threat actor references and summarize them with links. Those with limited understanding of the actor can quickly browse recent reporting with the option to dive further into the details of each case. As indicated in the final bullet point, there's mention of several other related ransomware threat actors including Storm-0464, Storm-0506, and Storm-0826. These are all great candidates to run back through this same Promptbook to further our understanding of a broader ransomware ecosystem.
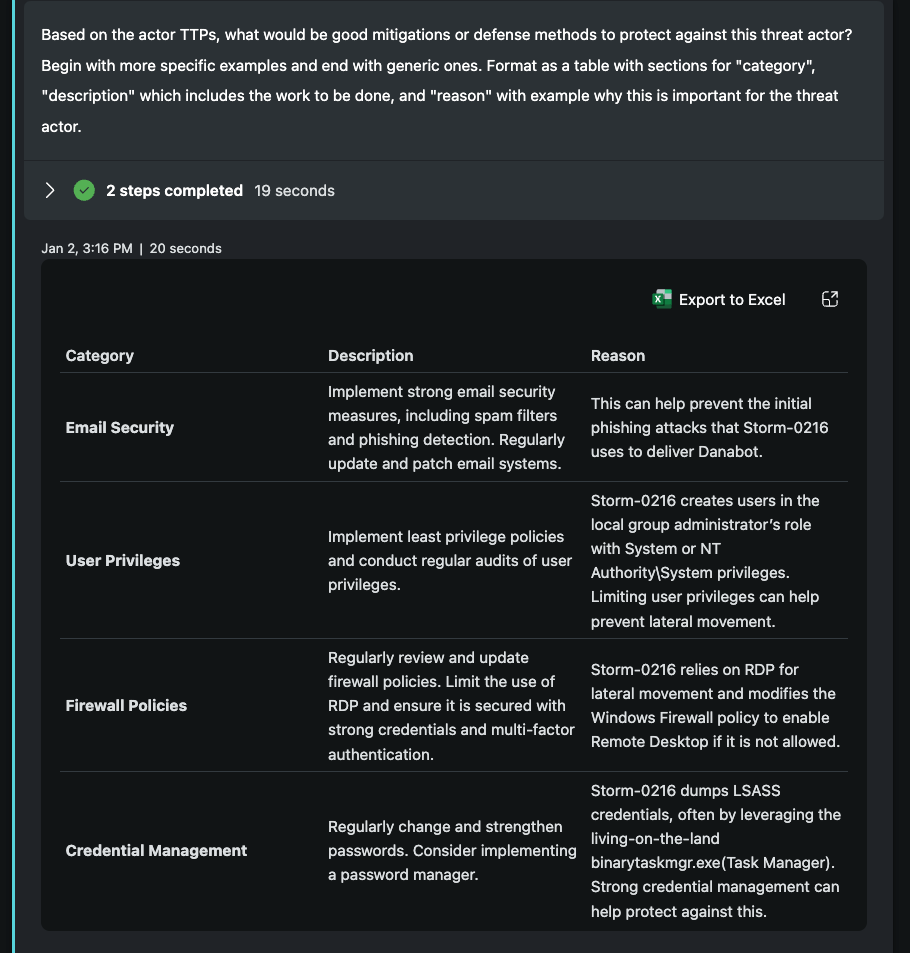
In this prompt, I shift back to more of a detailed prompt. Using the previous context formed from our broader session, I have Security Copilot outline mitigations and defense methods, starting with more specific first and ending with generic. This instruction is more open given the nature of the Promptbook, though could be tuned to an organization by incorporating technology leveraged or specific control-points of interest. I've instructed to focus on specific to generic as I've observed the model will often mix the both and while the generic is useful, it's not always the most actionable.
For the format, I've requested a table and included headers with a small amount of instruction. The response gives me what I want and while it's generic due to the structure of the request, it's worth appreciating how these seemingly generic steps are punctuated with threat actor specific reasons. Advising an organization to apply least privilege principles is much more impactful when given the note that a known ransomeware group will exploit this to move laterally and potentially wreak havoc on your organization. The former should be able to stand alone, but if that were true, ransomware wouldn't be as prolific.
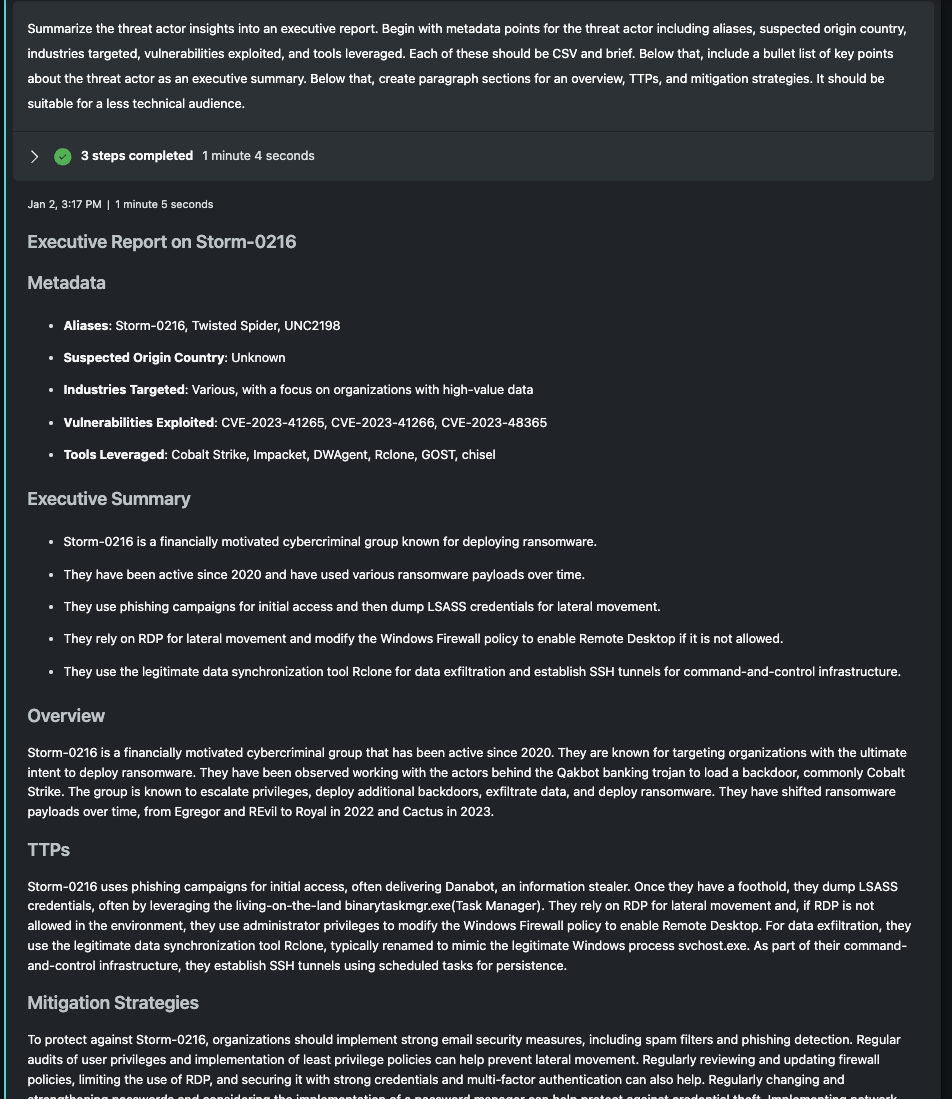
As a final step within this Promptbook, I ask Security Copilot for an executive report on the threat actor based on the session details. I request a metadata section that outlines common data seen across industry threat profiles including aliases, suspect origin country, industry targets, vulnerabilities exploited and tools leveraged. Below that is an executive summary formatted bullet points, followed by several narrative sections. This prompt could be further expanded to format the profile in the exact way an organization consumes data, but as it's written, it does a great first-pass.
Follow-on Questions
The end of a Promptbook doesn't mean the end of the session. In fact, I'd argue it's the beginning! Now that we have a grounded session containing a bunch of information about this threat actor, what additional follow-up questions could we ask? Here's a few that immediately come to mind for myself based on my past analyst experience.
- Provide a threat actor profile on all of the other actors associated with ransomware.
- Provide vulnerability impact assessments on all mentioned CVEs known to be exploited by the group.
- What other threat actors commonly target <your industry>?
- Summarize [Cobalt Strike, Impacket, DWAgent, Rclone, GOST, chisel] tools leveraged by this threat actor. Include ways to detect these tools within my environment, specifically using network signatures in Zeek format.
Operationalizing this Work
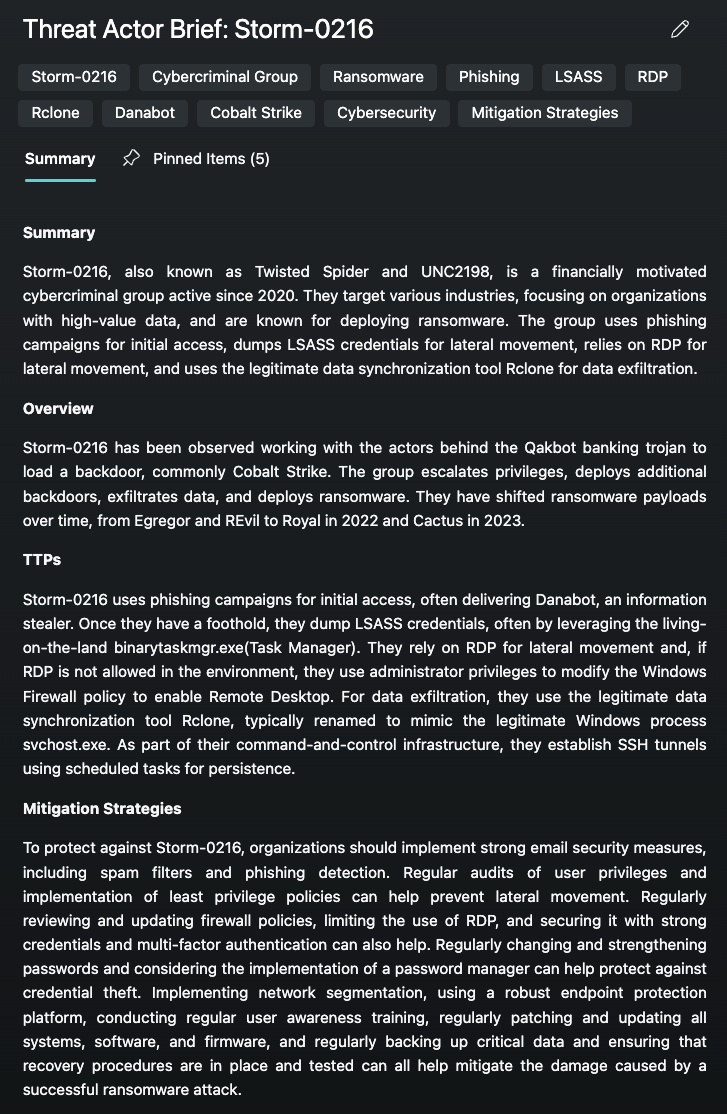
Building an understanding of a threat actor, specifically one that may be exploiting a ubiquitous vulnerability or one that delivers ransomeware, requires expertise, access to quality intelligence and most importantly, time. The Threat Actor Profile Promptbook in Security Copilot, paired with Defender Threat Intelligence, saves analysts hours of work and gives them a stronger foundation to operate from. Generative AI brings an actionable component to this information and allows for the reporting to be tailored to your organization.
One way to operationalize this Promptbook would be to identify which threat actors commonly target your industry and attach this Promptbook to run on a weekly basis. Results from the Promptbook could be reformatted to meet your needs and merged into a knowledge base for future reference. You can leverage the out-of-the-box Security Copilot version of this Promptbook or design your own to match your specific needs.
What I enjoy most about this Promptbook is the fact that it of course runs well on any Microsoft named threat, but it will also take alternative aliases from other company naming conventions and function on those as well. Years ago, when I did espionage research, I had to use a spreadsheet as a "rosetta stone" of threat actor names. I am hopeful that solutions such as this can begin to replace those older methods and allow defenders to focus on what matters most in their organization.